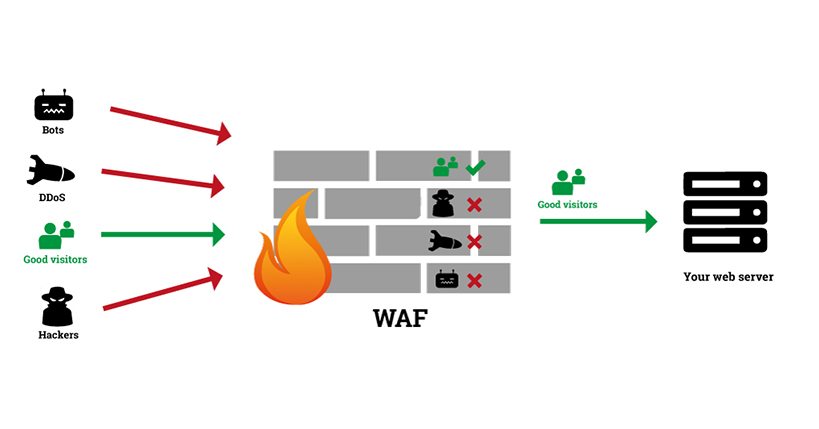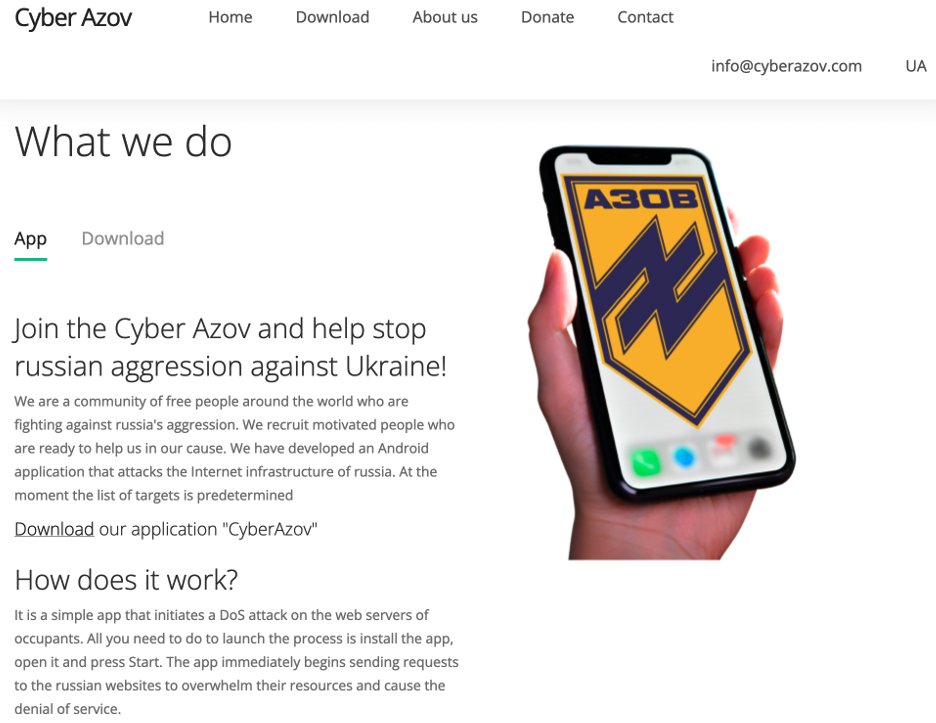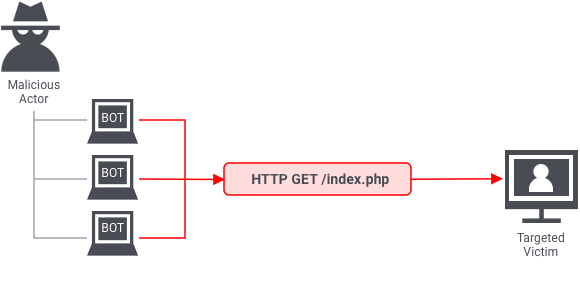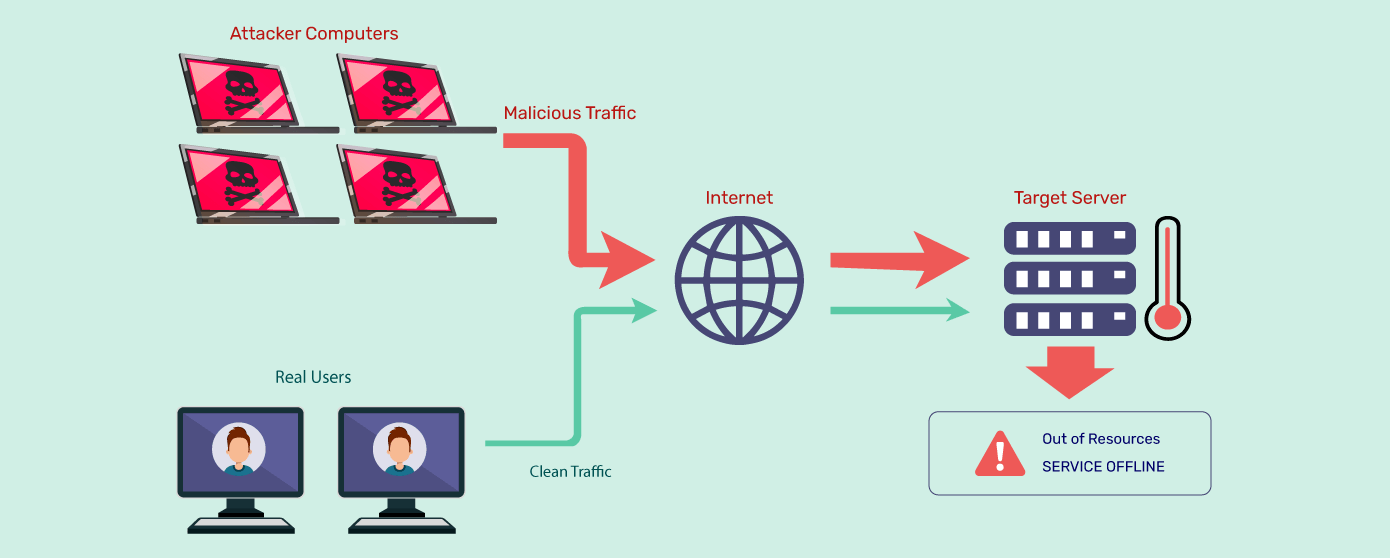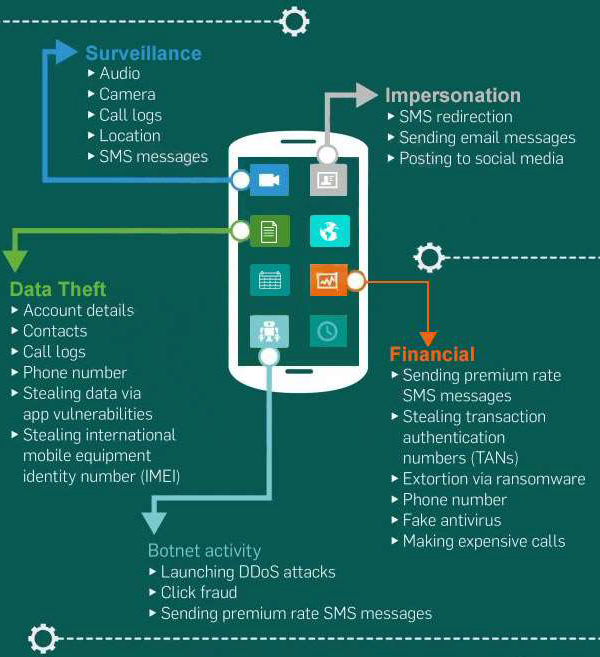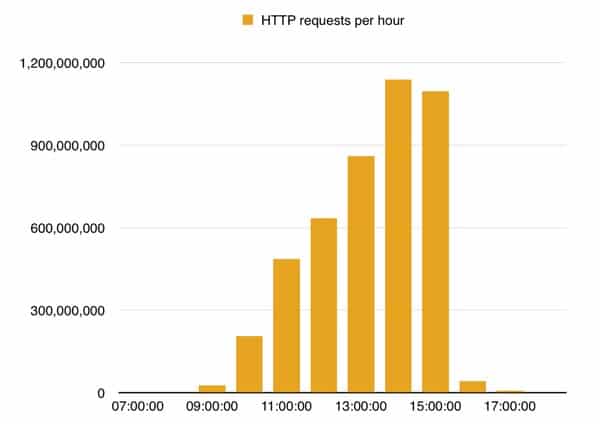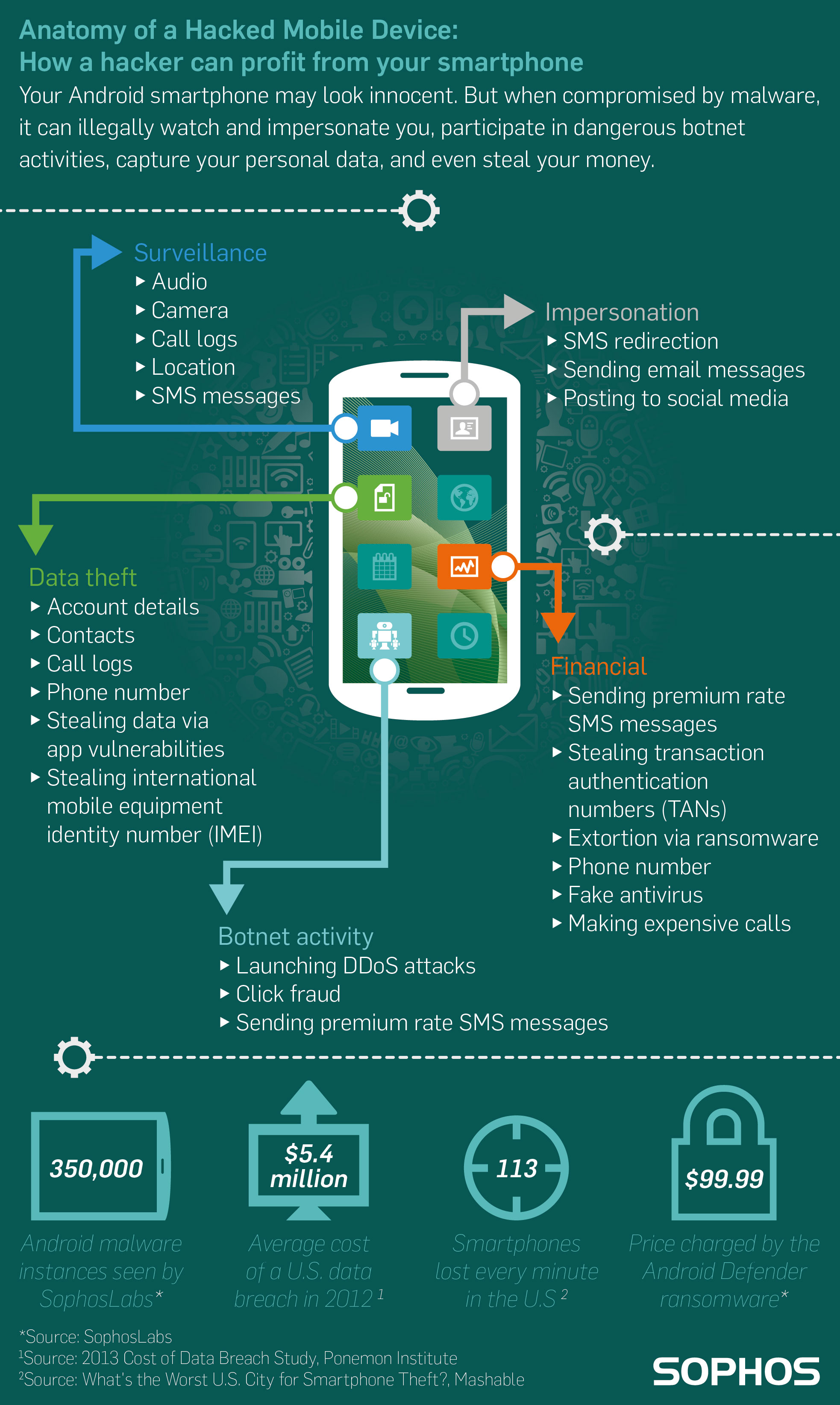
A New Trend of DDoS Attacks: Mobile Devices Are Becoming a New Generation of Botnets - Alibaba Cloud Community

Cloudflare claims pro-Russian hacktivist groups launched DDoS attacks on Australian organizations | Digital Watch Observatory
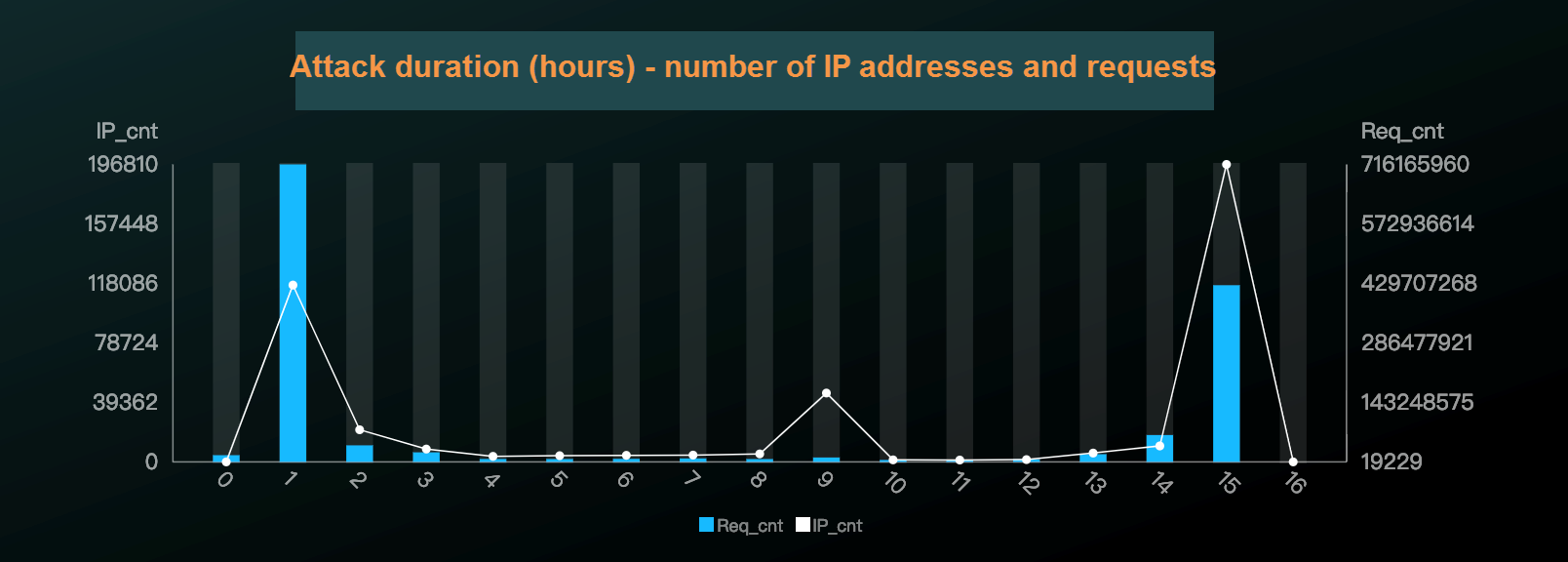
A New Trend of DDoS Attacks: Mobile Devices Are Becoming a New Generation of Botnets - Alibaba Cloud Community

DDoS Attacks on Mobile Networks {infographic} - Arbor Networks | Ddos attack, Networking infographic, Wireless networking

Jordan Daley on X: "This DDoS attack is serious. It has taken down Instagram, Facebook, T-Mobile, Verizon, and Twitch.... 2020 is something else. https://t.co/ztU59XMWu3" / X
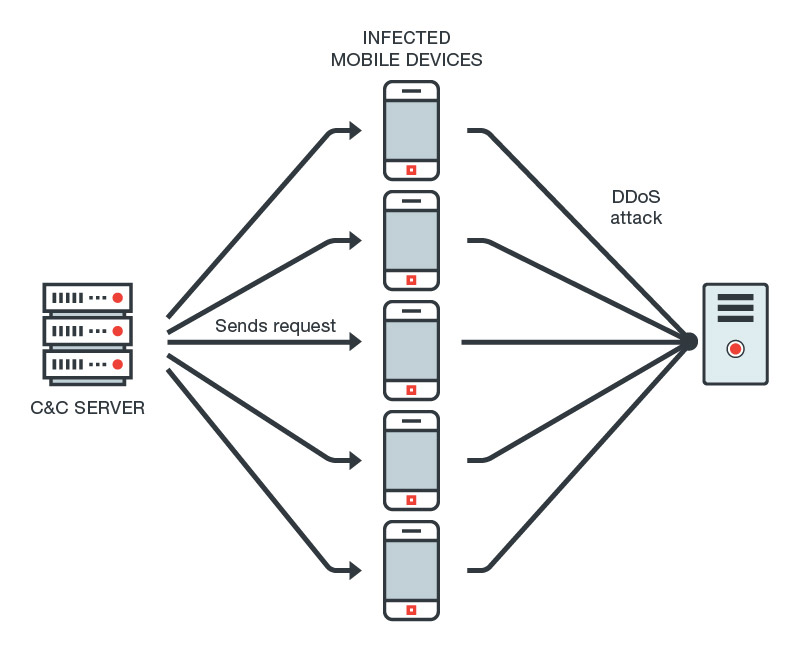

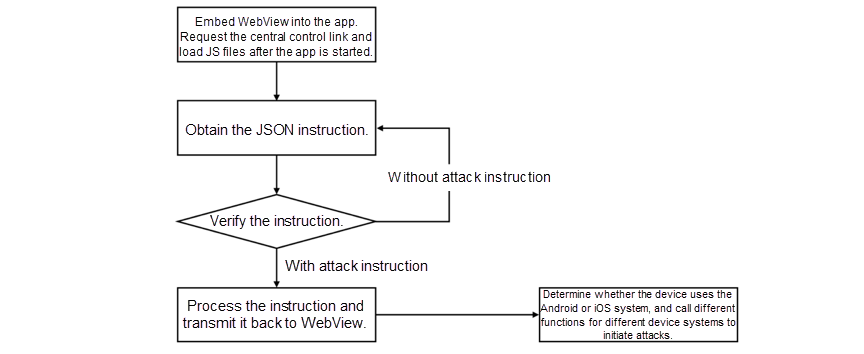
![PDF] Towards the Detection of Mobile DDoS Attacks in 5G Multi-Tenant Networks | Semantic Scholar PDF] Towards the Detection of Mobile DDoS Attacks in 5G Multi-Tenant Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/44639570f2cb62d6110832e6a8e8f74cc18492e6/2-Figure1-1.png)